「Windowsの移動ユーザープロファイル」の版間の差分
| 61行目: | 61行目: | ||
* 新しいシェアを作成してください。 詳細については、[[Windows ACLs を利用して共有を設定する]]を参照してください。 以下の権限を設定します。 | * 新しいシェアを作成してください。 詳細については、[[Windows ACLs を利用して共有を設定する]]を参照してください。 以下の権限を設定します。 | ||
:* | :* 共有の権限: | ||
::{| class="wikitable" | ::{| class="wikitable" | ||
!Principal | !Principal | ||
| 105行目: | 105行目: | ||
These settings enable members of the <code>Domain Users</code> group to store their roaming profiles on the share, without being able to access other user's profiles. Members of the <code>Domain Admins</code> group are able to access all directories on the share. | These settings enable members of the <code>Domain Users</code> group to store their roaming profiles on the share, without being able to access other user's profiles. Members of the <code>Domain Admins</code> group are able to access all directories on the share. | ||
== Using POSIX ACLs on a Unix domain member == | == Using POSIX ACLs on a Unix domain member == | ||
2019年3月3日 (日) 21:24時点における最新版
はじめに
Windowsプロファイルは、ユーザーごとの構成ファイルやレジストリ設定など、ユーザーのすべての設定を含む一連のファイルです。 Active DirectoryまたはNT4ドメインでは、ユーザーのプロファイルをサーバーに保存するように設定できます。 これにより、ユーザーは異なるWindowsドメインメンバーにログオンして同じ設定を使用できます。
ローミングユーザープロファイルを使用する場合、ユーザーがログインすると、プロファイルのコピーがサーバーからWindowsドメインメンバーにダウンロードされます。 ユーザーがログアウトするまで、すべての設定はローカルコピーに保存され、更新されます。 ログアウト中に、プロファイルがサーバーにアップロードされます。
Windows移動プロファイルのバージョン
オペレーティングシステムのバージョンに応じて、WindowsはユーザーがWindowsのバージョン固有の機能をサポートするために別々のプロファイルフォルダを使用します。 バージョン2以降のプロファイルでは、ユーザーのプロファイルフォルダに.V*という接尾辞が追加されます。
以下のWindowsプロファイルバージョンが存在します。:
Windows Client OS Version Windows Server OS Version Profile Suffix Example Profile Folder Name Windows NT 4.0 - Windows Vista Windows NT Server 4.0 - Windows Server 2008 none user Windows 7 Windows Server 2008 R2 V2 user.V2 Windows 8.0 - 8.1* Windows Server 2012 - 2012 R2* V3 user.V3 Windows 8.1* Windows Server 2012 R2* V4 user.V4 Windows 10 (1507 to 1511) Windows Server 2016 V5 user.V5 Windows 10 (1607 and later) V6 user.V6
- *デフォルト設定を使用すると、Windows 8.1およびWindows Server 2012 R2はV3プロファイルを使用します。 ただし、プロファイルはWindows 8.0およびWindows Server 2012とは互換性がありません。このため、Windows 8.1およびWindows Server 2012 R2をV4プロファイルを使用するように構成することをお勧めします。 詳細については、以下を参照してください。Windows 8.1ローミングユーザープロファイルと以前のバージョンのWindowsのユーザープロファイルとの間の非互換性。
ユーザーのプロファイルパスを設定するときは、必ずバージョンサフィックスを付けずにパスを設定します。 例えば:
\\server\profiles\user_name
Sambaファイルサーバーで共有を設定する
Windows ACLを使用する
Sambaファイルサーバーでローミングプロファイルをホストするためのprofilesのように、共有を作成するには、次の手順を実行します。
- 新しいシェアを作成してください。 詳細については、Windows ACLs を利用して共有を設定するを参照してください。 以下の権限を設定します。
- 共有の権限:
Principal Access Domain Users Change Domain Admins Full Control
- File system permissions on the root of the
profilesshare:
- File system permissions on the root of the
Principal Access Applies to Domain Users * Traverse folder / execute file
List folder / read data
Create folder / append dataThis folder only CREATOR OWNER Full control Subfolders and files only Domain Admins Full control This folder, subfolders and files SYSTEM ** Full control This folder, subfolders and files
- * You can alternatively set other groups, to enable the group members to store their user profile on the share. When using different groups, apply the permissions as displayed for
Domain Usersin the previous example.
- * You can alternatively set other groups, to enable the group members to store their user profile on the share. When using different groups, apply the permissions as displayed for
- ** For details, see The SYSTEM Account.
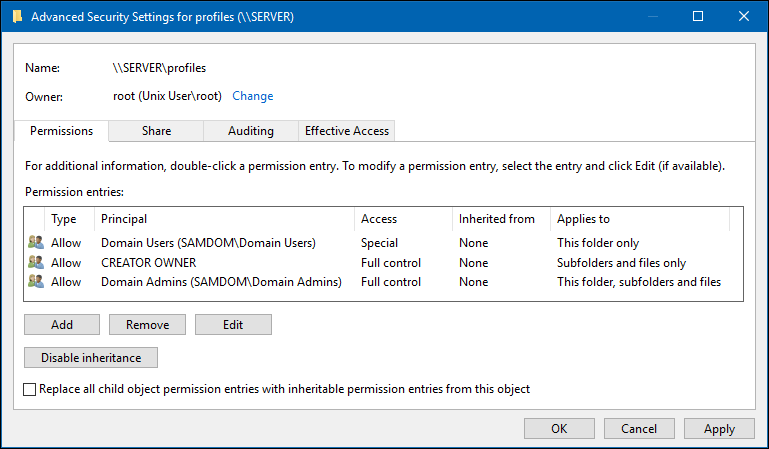
- Verify that permission inheritance is disabled on the root of the share. If any permission entry in the
Advanced Security Settingswindow displays a path in theInherited fromcolumn, click theDisable inheritancebutton. On Windows 7, unselect theInclude inheritable permissions from this object's parentcheck box to set the same setting.
- Verify that permission inheritance is disabled on the root of the share. If any permission entry in the
These settings enable members of the Domain Users group to store their roaming profiles on the share, without being able to access other user's profiles. Members of the Domain Admins group are able to access all directories on the share.
Using POSIX ACLs on a Unix domain member
On a Unix domain member server, you can set up the profiles share using POSIX ACLs instead of using Windows access control lists (ACL). This will not work on a Samba Active Directory Controller.
{{#invoke:Message box|imbox}}
- Add the following share configuration section to your
smb.conffile:
[profiles]
comment = Users profiles
path = /srv/samba/profiles/
browseable = No
read only = No
force create mode = 0600
force directory mode = 0700
csc policy = disable
store dos attributes = yes
vfs objects = acl_xattr
- For details about the parameters used, see the descriptions in the
smb.conf(5)man page.
- Create the directory and set permissions:
# mkdir -p /srv/samba/profiles/ # chgrp -R "Domain Users" /srv/samba/profiles/ # chmod 1750 /srv/samba/profiles/
- These settings enable members of the
Domain Usersgroup to store their roaming profiles on the share, without being able to access other user's profiles. Alternatively, you can set a different group.
- Reload Samba:
# smbcontrol all reload-config
Assigning a Roaming Profile to a User
Depending on the Windows version, Windows uses different folders to store the roaming profile of a user. However, when you set the profile path for a user, you always set the path to the folder without any version suffix. For example:
\\server\profiles\user_name
For further details, see The Windows Roaming Profile Versions.
Note that you must not set a trailing backslash.
In an Active Directory
Using Active Directory Users and Computers
In an Active Directory, you can use the Active Directory Users and Computers Windows application to set the path to the user's profile folder. If you do not have the Remote Server Administration Tools (RSAT) installed, see Installing RSAT.
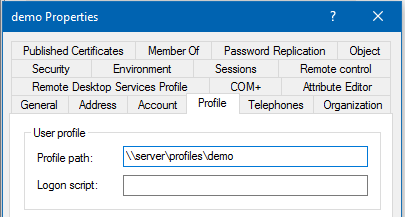
To assign \\server\profiles\demo as profile folder to the demo account:
- Log in to a computer using an account that is enabled to edit user accounts.
- Open the
Active Directory Users and Computersapplication.
- Navigate to the directory container that contains the
demoaccount.
- Right-click to the
demouser account and selectProperties.
- Select the
Profiletab.
- Fill the path to the home folder into the
Profile pathfield.
- Set the path always without any profile version suffix and without trailing backslash. For details, see The Windows Roaming Profile Versions.
- Click
OK.
The setting is applied the next time the user logs in.
Using a Group Policy Object
Using group policy objects (GPO), you can assign settings to organizational units (OU) or to a domain. This enables you, for example, to automatically assign profile paths to all users that log on to a computer that is a member of the OU or domain. If you move the computer to a different OU or domain, the setting is removed or updated. Using this way, you do not have to assign manually the settings to each user account.
{{#invoke:Message box|imbox}}
To create a group policy object (GPO) for the domain that automatically assigns the \\server\path\user_name path to every user that logs on to a Windows domain member:
- Log in to a computer using an account that is allowed to edit group policies, such as the AD domain
Administratoraccount.
- Open the
Group Policy Management Console. If you are not having the Remote Server Administration Tools (RSAT) installed on this computer, see Installing RSAT.
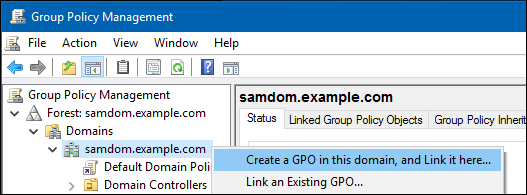
- Right-click to your AD domain and select
Create a GPO in this domain, and Link it here.
- Enter a name for the GPO, such as
Profiles on server. The new GPO is shown below the domain entry.
- Right-click to the newly-created GPO and select
Editto open theGroup Policy Management Editor.
- Navigate to the
Computer Configuration→Policies→Administrative Templates→System→User Profilesentry.
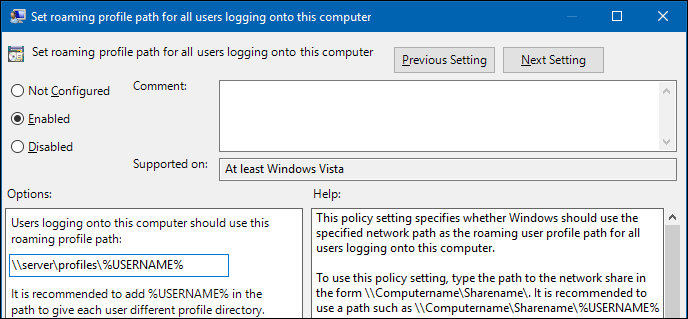
- Double-click the
Set roaming profile path for all users logging onto this computerpolicy to edit:
- Enable the policy and set the profile path. For example:
\\server\profiles\%USERNAME%
- Windows replaces the
%USERNAME%variable with the user name during login. Set the path without trailing backslash.
- Windows replaces the
- Click
OK.
- Click
- Close the
Group Policy Management Editor. The GPOs are automatically saved on theSysvolshare on the domain controller (DC).
- Close the
Group Policy Management Console.
The GPO is applied at the next reboot of the Windows domain members or when they reload the group policies.
Using ldbedit on a Domain Controller
On a domain controller (DC), to assign, for example, the \\server\profiles\demo\ path as profile folder to the demo account:
- Edit the
demouser account:
# ldbedit -H /usr/local/samba/private/sam.ldb 'sAMAccountName=demo'
- The accounts attributes are displayed in an editor. Append the following attribute and value to the end of the list:
profilePath: \\server\profiles\demo
- You must not set a trailing backslash to the path.
- Save the changes.
The setting is applied the next time the user logs in.
In an NT4 Domain
In an Samba NT4 domain, to set \\server\profiles\%U as path to the profile folder:
- Add the following parameter to the
[global]section in yoursmb.conffile:
logon path = \\%L\Profiles\%U
- During logging in to the domain member, Samba automatically replaces the
%Uvariable with the session user name. For further details, see theVariable Substitutionssection in thesmb.conf(5)man page.
- Reload Samba:
# smbcontrol all reload-config